In today's digital age, where data breaches and privacy concerns are increasingly becoming the norm, the importance of robust privacy and data protection cannot be overstated. This reality has transformed confidentiality and data protection from mere compliance checkboxes to strategic imperatives for businesses and organizations. It's more than just avoiding financial repercussions; it's about forging trust with your clientele, bolstering your brand's image, and securing your company's future.
This blog post is designed to guide you through the process of advancing your privacy and data protection initiatives. With a focus on practical, actionable steps and the ethos of continual improvement, you can ensure your data protection strategies are not only functional but also resilient. Let's explore how to adeptly elevate your program to face the challenges of the modern digital world.
Assessing Your Starting Point
Firstly, understanding where you currently stand is vital. A detailed assessment of your existing data privacy and protection measures is the first order of business. This entails examining your policies, processes, and technologies related to data management comprehensively. Additionally, it's imperative to grasp the nature of the data you collect, its usage, storage locations, and access permissions. From this base knowledge, a Data Privacy Program Design can be effectively developed to guide your enhancements.
Defining Your Objectives
Next, establishing clear, actionable objectives for your privacy program is critical. What are the specific outcomes you aim to achieve? Objectives range from ensuring compliance with regulations like GDPR or CCPA to minimizing the risk of data breaches. Setting distinct goals allows you to customize your Data Privacy Program Design to meet these aims, ensuring every step is closer to your desired state.
Enhancing Employee Training and Awareness
Moreover, evolving your privacy and data protection efforts significantly involves ongoing training and raising awareness among all staff members. Since human error is a significant vulnerability in data security, integrating data protection principles into your company culture is essential. Making Data Privacy Program Design a part of continuous training efforts not only underscores the importance of privacy but also empowers your team to protect sensitive information effectively.
Adopting Advanced Technologies
Furthermore, technology is a cornerstone in strengthening privacy and data protection programs. The right technological tools, such as encryption, tokenization, access controls, and monitoring solutions, can dramatically lower the risk of data breaches. It's crucial to periodically review and upgrade your technological arsenal to align with current data protection standards. Embedding technology into your Data Privacy Program Design not only fortifies your defenses but also makes compliance and reporting more efficient.
Committing to Ongoing Monitoring and Improvement
Additionally, the digital landscape is ever-evolving, with new threats emerging constantly. Thus, your privacy and data protection program must be agile ready to adapt to new challenges. Committing to continuous monitoring of your data protection measures enables you to identify and rectify vulnerabilities swiftly. Regularly revising your Data Privacy Program Design ensures its ongoing effectiveness and compliance with changing regulations and standards.
Building a Privacy-First Culture
Importantly, cultivating a culture that prioritizes privacy is foundational to the success of your program. This means embedding privacy into the core values of your organization beyond just compliance. It involves clear communication about the value of privacy, engaging employees in privacy initiatives, and showing leadership's commitment to data protection. When privacy is a core value, it enhances your Data Privacy Program Design's effectiveness and builds trust with customers and stakeholders.
Preparing for Potential Incidents
Despite the best preparations, incidents may still occur. An evolved privacy and data protection program includes comprehensive incident response plans. These should detail procedures for detecting, reporting, and managing data breaches. A swift and effective response not only mitigates the impact of breaches but also shows regulators and the public your serious stance on data protection. Including incident response in your Data Privacy Program Design is crucial for resilience.
Encouraging Widespread Collaboration
Lastly, enhancing your privacy and data protection program is not solely the responsibility of the IT department. It demands collaboration across the entire organization. Effective communication about policies, procedures, and responsibilities ensures collective alignment and the pursuit of shared goals. By promoting collaboration, your Data Privacy Program Design becomes a unified effort, strengthening your comprehensive approach to data protection.
Wrapping Up
To conclude, evolving your privacy and data protection program is a continuous journey of adaptation and improvement. It starts with a clear understanding of your current position, followed by establishing clear objectives, and requires the entire organization's commitment. You can develop a robust and resilient data protection program by integrating ongoing training, leveraging advanced technology, committing to continuous monitoring, fostering a privacy-first culture, preparing for incidents, and encouraging collaboration.
In our current digital environment, ensuring data protection is a regulatory necessity and a pivotal component of your business strategy. A robust privacy and data protection program protects against risks, builds trust with your customers, and enhances your reputation. As you move forward, bear in mind that every step towards strengthening your privacy efforts is a step towards a more secure and trusted future for your organization.
























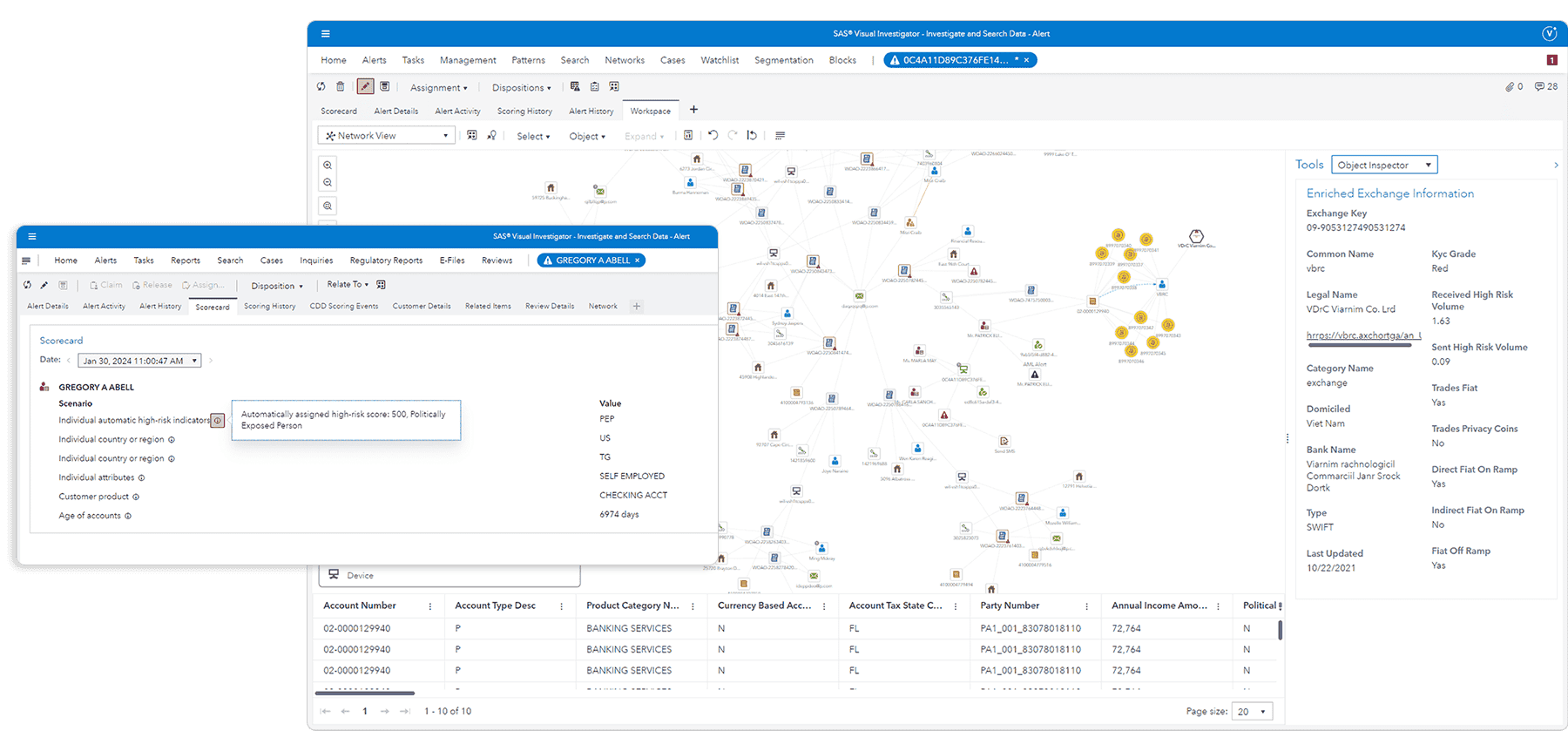







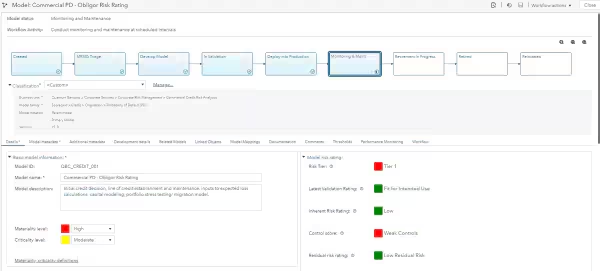









.webp)

-1.jpg)










.jpg)



























.jpeg)







